The real impact of an onchain hack
A comprehensive study of hack damage from 2021 to 2023
How much does an onchain hack really cost?
To date, no one really knows. But could discover a predictive estimate by analyzing historical hacks. In this post we’ll go through the historical data of the last several years to build a representative estimate for the typical future hack across impact categories (it’s not just money stolen). From there, we’ll create a heuristic for estimating what the typical hack would cost your favorite protocol, which I’ll call Amador’s hack impact estimate.
Before we begin, do me a favor and hit the Subscribe button (it’s free!) to receive my future research (typically on a monthly cadence). Thanks for your support!
Summary:
To date, no one had a great estimate on the expected cost of an onchain hack, and that’s unfortunate. But we can make one by statistically analyzing hacks over the last few years! I analyzed hacks from 2021 to 2023 to come to a representative estimate of the real cost of an onchain hack. Let’s call it Amador’s hack impact estimate.
Amador’s hack impact estimate: if your protocol gets hacked, you should expect to lose approximately $16,000,000 USD, see your token price decline by 52% of market cap, expect depressed token prices to persist for at least 6 months (and likely much longer), and lose 3 months of time and effort recovering.
If your product is a platform (either as a L1/L2 blockchain or a financial primitives protocol), expect your protocol and its dependents to be wiped out as suggested by antecedent cases like Terra-Luna.
We aggregated these findings together at https://stats.immunefi.com/. Go check it out! We’ll be adding more statistics and datapoints there as they become available.
But let’s back up: the first shocking thing is that we don’t have good hack impact estimates today, despite crypto suffering hundreds of hacks in the last three years alone. For that, we must blame the difficulty of measuring the true impact of a hack.
The reality is that net value stolen, which is the standard widely used figure, grossly underestimates the damage caused. It misses all the other ways hacks wreak damage, many of which are more financially damaging than the hack itself, though they are more difficult to quantify. The contributors to total hack damage that are most unrecognized by non-security practitioners are:
Market impact: Market impact is the damage to the publicly trading token (or hypothetically equity) prices caused by the hack, which can last over long periods of time. This impact is much less known than the value immediately hacked, and its importance remains under-appreciated by most security practitioners.
Dependency impacts: Dependency impact refers to second-order effects stemming from the original hack that cause damage to other assets. There are three major categories of dependency impact: Platform dependency, financial dependency, and reputational impact. The hack of a blockchain itself in such a way that it compromises all assets/contracts built on that blockchain is an example of platform dependency impact. The decline in Luna pricing destroying the value of the Terra stablecoin is a good example of financial dependency impact (though it is not a hack in the way most DeFi hacks are). Perceived lack of security of a platform (such as with BNB Chain) that diminishes user growth and adoption of that platform is an example of reputational impact.
Talent & organizational impact: Damage here is challenging to quantify, typically taking the form of lost time, money, and talent due to post-hack response and recovery. Given that a hack and its recovery can consume months of work for a small startup team, the organizational impact alone is always costly and sometimes fatal. All but the most preemptively prepared organizations must deal with this impact post-hack.
In other words, the typical hack is much more damaging than mere funds stolen would suggest!
The remainder of this article describes estimates for assessing each type of impact in the case of a typical hack by looking at historical medians or, where data is unavailable, by making an estimate informed by my firsthand experience.
Impact from funds stolen
The data tell us there were 107 hacks in 2021, 134 hacks in 2022, and 247 hacks in 2023, for a total of 488 publicly known hacks from 2021-2023.
These hacks impacted $2,334,863,067 USD in 2021, $3,773,906,837 USD in 2022, and $1,699,632,321 USD in 2023, for a total of $7,808,402,225 in funds impacted from 2021-2023.
For clarity, funds impacted means funds hacked, stolen, or otherwise lost, but it doesn’t include funds returned or reclaimed by whitehats and investigators.
Using these numbers, some simple math on this 2021 to 2023 dataset gives us the following insights:
The average hack resulted in the theft of $16,000,824 USD
The median hack resulted in the theft of $1,000,000 USD
There is a power law distribution to hacks; many hacks are small, but when the big ones happen, they are a hundred times larger than the median hack.
Market impact
Estimating market impact has been a historical challenge. Immunefi made the very first such report, found here, reviewing hacks and their impact in 2022 on a sample of 63 hacks from 2022. This sample showed an average drop in underlying token price of 13% 2 days after a hack and an average drop of 19.5% 5 days after a hack.
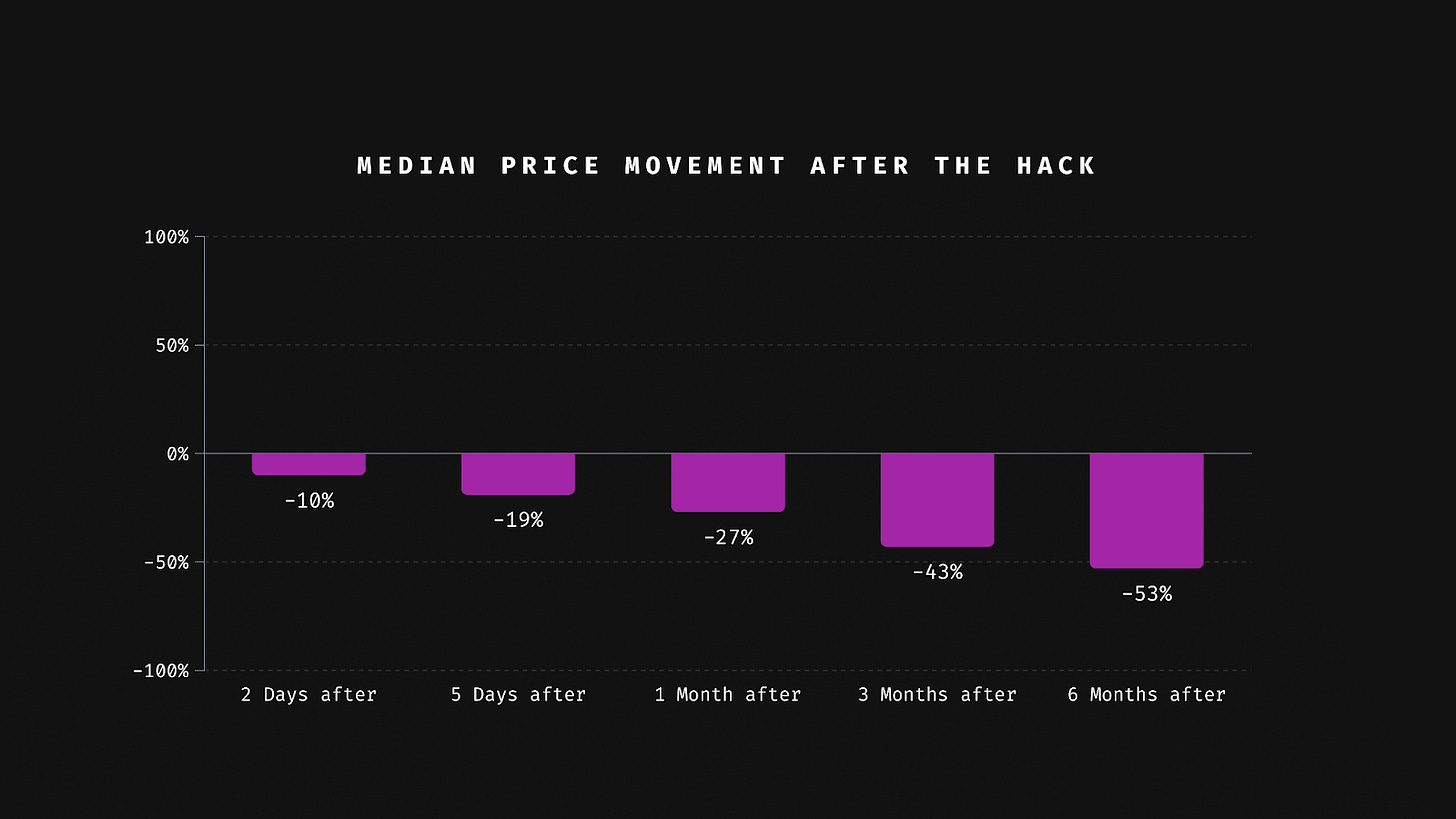
To flesh out our review, we decided to update this dataset with as many of the 2021, 2022, and 2023 hacks as we could collect evidence for. We'll refer to median price movements moving forward. With the extended dataset, the median is a more predictable estimate considering rare outliers that could grow or drop much more severely.
The new dataset covers a total of 176 hacks. The results are pretty shocking:
The data shows median price declines and prolonged price depression post-hack of:
-10% two days after the hack,
-19% five days after the hack, and
-27% one month after the hack
-43% three months after the hack
-53% six months after the hack
Looking past the median toward the most severe cases, the results are even more staggering. Three months after the hack, 32% of hacks had token declines in excess of 50%, and 11% had declines over 90%. Six months after the hack, 35% of hacked projects continued to experience sustained price declines of over 50%, and 16% had declines over 90%.

This showcases the power law distribution of hack impact and that a single, severe hack can be fatal. Moreover, it shows that hack impact intensifies over time, inflicting ongoing market impact for at least six months post-hack.
It is likely that the market impact continues to intensify to the 1-year mark, but as our dataset covers only three years worth of hacks, we will have to wait until 2024 numbers are fully tabulated before validating that hypothesis.
A caveat: we can’t be 100% sure that this impact is caused by hack impact. Any number of factors can put downward pressure on token prices, including ones that we might not be aware of in this study. The most obvious confounding factor is token price correlation with macro market conditions. But the numbers are so severe and striking as to suggest that they are primarily hack-derived, and so that’s the position we’re taking.
Reviewing all the data together, we’d expect the typical hack to cause a median market impact to their token price of approximately -19% over the first five days and intensifying to -53% over the following six months (probably lasting indefinitely into the future), with a 16% chance of that damage being in excess of 90% of the project’s market cap.

Clearly, market impact can be pretty scary!
Once you appreciate that most token projects use their liquid tokens as treasury and growth fuel, you understand why security practitioners take market impact so seriously. Even if the hack doesn’t get you, too much market impact can prove just as fatal.
Dependency (or second-order) impacts
There is a major type of unappreciated hack impact, which we call dependency impact or occasionally second-order impact. It describes the cascade of damage triggered by the initial hack. A few examples of this type of impact:
Platform-dependent impact is the damage caused by the underlying platform going down (in a blockchain DoS attack, for example, that comprises money market or perpetuals markets living on top of affected platforms), which can wreak havoc on all applications operating on that platform. Despite its commonality (there are countless platforms in crypto), the limited links between the onchain and offchain economy have limited incidence of this type of impact to date, and the blockchains have proven themselves to be remarkably resilient pieces of technology. As the onchain and offchain economies link up, we should expect such impacts to become more common and severe.
Financial dependency impact concerns hacks that cause second-order impacts to dependent assets. Assets with financial dependency risk include stablecoins (like MakerDAO, CDP liquidations), liquid staking tokens (like LIDO, Rocketpool, etc), derivatives protocols (like Pendle), and almost any token paired on liquidity pools. Financial dependency impact is one of the harder categories to assess, as it can go easily unnoticed; almost any hack involving theft of tokens will create dependency on other tokens that are directly or indirectly related.
The quintessential example of dependency impact is the collapse of Terra-Luna. The financial attack on the stablecoin protocol’s equity token depegged the stablecoin and drove a downward spiral, from which it never recovered. The collapse of Terra-Luna destroyed not just the $40 billion USD in Luna equity, but also the $1 billion in outstanding UST Terra stablecoin, and all the value in Terra-Luna dependent DeFi, like the $1.5 billion USD equity value of the Anchor Protocol, alongside countless other Terra-based protocols. The harm to the Terra ecosystem was near total; the Terra ecosystem is 99% down today, basically defunct.
Some colleagues and I are actively engaged in research here to understand the true incidence of dependency impacts. Seeing that this research is in progress, we won’t draw premature conclusions by including the typical dependency impact in our rule on hack impact. When the research is done, we’ll share our findings here and update this post. Tentatively, dependency impacts appear to be much more severe than is commonly understood.
Talent and organizational impact
Talent and organizational impact typically take two forms: Loss of talent and operational or procedural changes.
Talent impact concerns personnel loss post-hack, either due to perceived fault or incompetence, a perceived need for fresh security talent, or demoralization as a result of the hack. Either way, it’s not uncommon for hacked projects to lose their former security leaders.
Compounding the problem, a hack makes it more challenging to hire new security leaders, as it signals organizational weakness.
The second form is unplanned operational or procedural investments (almost always security-oriented) made as a result of the hack. While these are positive, they slow down progress on the core product by distracting valuable attention from growth to security.
Quantifying impact here is challenging, but I do have some first-hand experience war rooming with a number of projects and will make estimates based on those experiences.
In my experience, the pre-hack security leadership is typically lost as a result of the hack. This could be a CISO, a security engineer, or even an engineering leader who was placeholding the security role. Their departure can be mutually agreed, as experiencing a hack on one’s own watch is a very demoralizing event, or it can be for cause. They also tend to be let go prematurely, in my view, because it will take an organization 1.5 to 4 months to hire an effective security replacement. This becomes lost time for the hacked project.
A hack also tends to freeze the team in a state of shock that far outlasts the hack itself. Organizations will devote themselves to at least two weeks of damage survey and control and two to three months of remedial security work (which suddenly becomes the most important thing on everyone’s to-do list), which will result in deprioritization of the core product roadmap.
The above example numbers are the more positive outcomes. Talent impact can be much more severe as it impacts the financial runway of a project, as exemplified by Kyberswap: In November 2023, KyberSwap suffered a $49M exploit. Understandably, they wanted to reimburse their users, but to do so, the team had to cut 50% of its workforce to keep the firm’s business operations up and paused its liquidity protocol initiatives and KyberAI project. The 10% bounty Kyber offered to the blackhat ultimately did not help.
It’s impossible to compute these impact factors into a simple impact calculation, so we’ll have to settle for summarizing the unique impacts and leave them as is: If you get hacked, expect to burn 3 months on remedial security work, lose 3 months of progress on your core product roadmap and objectives, lose your present security leader, and get a replacement for them 3 months later. It’s as if 3 months of effort are lost into the ether. This is some intense damage for any startup, although it is not typically fatal.
So, what’s the cost of a hack?
Pulling it all together, we now have the data to build out our estimate. Let’s sum it up in order of the quantified damage and severity:
The average hack impacts $16,000,000 USD million at the moment of exploit.
The median hack causes a dramatic 52% price decline in the underlying token market capitalization over 6 months. 79% of hacked projects continue to experience price depression 6 months later, with the ultimate duration of this hack-induced market impact being unknown and possibly indefinite.
The median hack does not create dependency impacts of either a financial or platform nature, but when such impacts do occur, they tend to be absolutely catastrophic, risking total destruction of assets dependent on the underlying platform. In critical bug reports with dependency impact of either kind, the typical potential impact is up to the sum total of extractable value on that platform!
While harder to estimate, the median hack should cause around 3 months of lost time and effort across remedial security work, lost roadmap time, team churn and replacement, the loss of whoever is the present security leader, and a great deal of anxiety in attempting to ensure you never get hacked again.
We now have everything we need to create a simple rule for assessing the real cost of an onchain hack. If your protocol gets hacked:
Expect value stolen of approximately $16,000,824 USD
Expect price suppression of 52% of your token’s market cap, and for that price suppression to last at least 6 months, and expect to never recover from this price suppression (77.8% of hacked tokens appear show sustained price suppression 6 months later)
Expect to lose 3 months of time and effort recovering and rebuilding post-hack
A corresponding real-life example of the above estimate is the Indexed Finance hack, in which $16 million USD was stolen on October 14, 2021. The token market cap was $11m at the time of the hack, and was $3.8m 6 months later, showing sustained price depression post-hack. The team never fully recovered from the incident, and Indexed Finance was basically dead by mid-2022. So, our estimate of probable hack impact appears to predict hack impacts effectively.
If your product is a platform (either as a L1/L2 blockchain or a financial primitives protocol) and you get hacked, the typical hack severity profile is one of absolute fatality: your protocol and its dependents are at risk of being entirely wiped out.
Scary stuff.
Concluding thoughts
Getting hacked is the beginning of the damage, not the end. The millions lost to the hack immediately anticipate even larger losses, caused by market impact and dependency impact, alongside many months of lost time spent rebuilding your emotionally shattered team and operations. Not fun.
There is no solution to these problems except investing in onchain security and progressively hardening our entire industry.
Of those measures, bug bounties are the most quantifiably proven to prevent hacks and hack impact at massive scale. I’ve done a quick review on the impact of bug bounties in demonstrably preventing tens of billions in hacks, and you can read more about that here in my Retrospective on Immunefi.
But looking beyond that, we need more and better code review from more 100x hackers, more and better security standards, and more and better automated security technologies. Only hardening across the stack will prevent hacks.
That’s what we’re building at Immunefi: effective security across every layer of the onchain security stack until hacks become a thing of the past.
If you like my blog, please subscribe & share it with your friends. I write in my free time, so seeing more people read these posts motivates me to write more. I don’t send anything except my research, typically monthly.