Before we begin, do me a favor and hit the Subscribe button to show me you value my writing for you. Thanks for your help!
I run Immunefi, the main clearinghouse for onchain exploits. Every day, thousands of hackers hunt on Immunefi, safeguarding key onchain infrastructure by turning unexpected vulnerabilities into exploits in supposedly secure code. Having seen the vulnerabilities and run the statistics, I can confirm what we’ve all felt: Blockchain security impact (as measured by protecting projects from harm and users from theft, in hard $dollars) comes from a select few hackers, the hackers so impossibly good that they are more impactful than a hundred other security researchers put together.
I call these security researchers ‘100x hackers’ because these hackers have, quite literally, 100x the positive security impact of the typical security researcher, sometimes even 100x the impact of other elite-level hackers.
100x hackers find more vulnerabilities, and they do so faster than their peers. They find vulnerabilities no one else could have–the kind lurking in open code for years on end. The best part is that with bug bounties, we can measure the direct and tangible impact of 100x hackers and compare them to one another. There are people on Immunefi’s Whitehat Leaderboard who have discovered multiple critical vulnerabilities, saved hundreds of millions of dollars (even billions), and earned life-changing millions.
This discussion isn’t meant to knock on the typical security researcher who makes an invaluable contribution to the onchain economy in his own right. The typical security researcher stands far above most blockchain developers in their ability to find vulnerabilities and secure code; professional security researchers regularly show outsized ability to prevent catastrophic harm in the code they protect, making them very valuable team members. They do the lion's share of code review and red-teaming (inclusive of auditing) that keeps the onchain economy safe. Without them, hacks would be far more frequent.
To give you a quantitative baseline, the typical security researcher on Immunefi makes a real contribution to ecosystem security, submitting an average of 11.69 vulnerability reports per year across the severity range, and this while working on an overwhelmingly part-time basis. Moreover, these typical security researchers make up the vast majority of crypto’s auditor workforce as the frontline keeping bugs out of production. Auditing has proven so effective that getting audits prior to new deployments is a widely respected industry standard.
Clearly, protocols can and should do whatever they can to attract and engage as many professional security researchers as they can.
And yet, 100x hackers remain in a league of their own. I’ve analyzed Immunefi’s own data, which is by far the most comprehensive in the space, to show you a picture of what these 100x hackers look like.
The numbers speak for themselves.

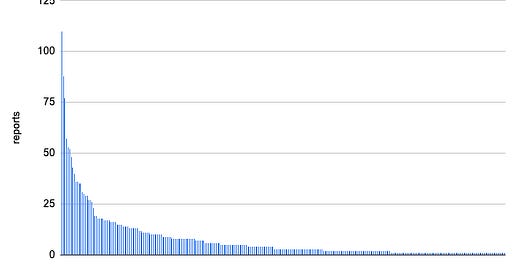
If ever there was any proof needed to show the existence of 100x hackers, here it is. The top hackers disclose far more criticals than others (many multiples of the median). Note that this graph only includes elite-level security researchers; even among elites, 100x hackers stand apart.

Their earnings reflect a similar pattern of outsized performance; note that this graph does not have few entries; it’s just that the largest earners outstrip everyone else by a vast margin.
The onchain economy survives because of these 100x hackers, who have prevented countless billions in losses that would have otherwise destroyed the legitimacy of the crypto marks. Every independent security researcher should strive to become one of them.

These graphs prove the 100x hacker’s existence through the metric that matters most: Positive security impact through funds saved and harm prevented, shown logarithmically. Note: This data comes from a narrow sample of 33 bugfix reviews, made public on our blog. It does not include the entire dataset of reports (which is thousands of vulnerabilities, most of whom have not had impact quantified due to how labor-intensive that work is). Note the dropoff into the millions in funds saved, the result of an artificial cut on our side; there were some hundreds more cases accounting for single-digit million saves, a milestone which most elite security researchers on Immunefi have achieved.
Funds saved reflects the true, differentiating marker of the 100x hacker, which is that they can find unique vulnerabilities, understand how to turn them into catastrophically dangerous exploits, and responsibly disclose them to prevent 100x (or much more) the damage of the typical security researcher. And they repeat this immensely challenging security feat over and over again.
Before we further explore the profile of the 100x hacker, and how you might learn to become one, it’s worth exploring the link between the 100x hacker and the 10x developer.
For those unaware, the 10x developer is a hypothetical engineer who is 10x more effective than the typical software engineer. Many people claim to have worked with one of these rare talents. Others doubt their existence. They get their incredible output from their vast knowledge of computer science and the software stack, applying just the right solution at just the right time–and quickly. The end result of their superior skills is the capacity to produce 10x the output of the typical developer. They can do this because programming is not effort-dependent, but rather knowledge-dependent. You can achieve many tasks in 1,000 SLOC, or you can do it in 10,000 SLOC. It all depends on what you know.
There are similarities between these profiles since the 100x hacker is knowledge-dependent in a similar way. Their vast knowledge of existing vulnerability and exploit patterns, onchain primitives and blockchain architectures, and the various security tools at hand make them capable of massive security impact.
But where the 10x developer’s impact scales with their production, the 100x hacker’s security impact scales with their ability to surface potential harm. In crypto, the capacity for harm scales so massively as to make their impact uniquely valuable. The classic example of this is the $billion dollar vulnerability, of which there have been a number in the history of DeFi and on Immunefi.
But this takes us to the most important question: how does one become a 100x hacker? Is there a replicable method? To find out, I’ve spoken to many of these 100x hackers working on Immunefi, who were generous enough to answer my questions. To summarize my conclusions, derived from a mixture of these interviews and my own profiling conclusions, the 100x hacker is characterized by:
A deep knowledge of computer science and blockchain fundamentals. A strong, intuitive mastery of the fundamentals is a prerequisite for high-level hacking skills. You cannot fully exploit what you do not understand.
Strong mathematics and coding skills. At the highest levels of vulnerability detection, analysis, and exploit packaging, strong math skills play a crucial role. Note that 100x hackers are not necessarily the best developers, but they do understand development very well. Sophisticated hobby projects are very common with them, as the flip side of the urge to break or disassemble is the urge to create.
A comprehensive knowledge of vulnerability patterns, attack vectors, and exploit design principles, unique to their focus area and personal interests. Encyclopedic knowledge of these areas allows them to find innocuous hooks and turn them into full-blown exploits. Because such knowledge is typically field-dependent, it often emerges from day-to-day work or personal interests, and takes countless hours to build.
High creativity, with an eccentric and often divergent mindset. 100x hackers are very independently minded; they have to be in order to hunt and find what no one else has found. Living this way results in unique perspectives and eccentricities. This is one of the most defining characteristics of the 100x hacker, as they have creativity in far greater abundance than most of their peers.
A high tolerance for risk, the first of which is the willingness to risk one’s own time throwing their energy against ostensibly impossible-to-crack code, and the second of which is to devote one’s personal time and career to the task indefinitely. Becoming a 100x hacker requires a long period of research and work that can’t be rushed.
Tenacious grit and tolerance for pain. 100x hackers throw themselves against the castle wall of secured code over and over again. They give up on a target far later than others would.
An idealism, pro-social attitudes, and a strong sense of integrity, but in blackhat cases a deep skepticism of the prevailing systems of society and morality. Whether moral or amoral, they tend to go to extremes.

These atypical psychological factors drive their outsized security impact. Factors #1-4 give them the advantage of compounding knowledge, which lets them see what others can’t. Factors #5-7 give them the intense self-belief and tolerance for suffering necessary for trying repeatedly.
Given the demanding requirements of the above profile, it’s no wonder 100x hackers stand out. Becoming one is a long, multi-year journey with few upfront rewards or assurances of success.
And yet, 100x hackers can drive onchain security like nothing else can. We need more of them.
If you dedicate great effort to the fundamentals of blockchain security and cultivate your character and personal discipline, you can become like the best hackers in our industry. Over a long enough time, these factors should bring you to their level. I certainly think so. I’ve seen it a number of times now.
We built Immunefi for exactly this reason, and its operations revolve around attracting, nurturing, and incentivizing these rare 100x elite hackers. Today, we are proud to work closely with many of them. This cohort of elite security researchers is the single most potent security force in all of crypto, as the last three years of Immunefi critical vulnerability disclosures have shown.
The journey of becoming a 100x hacker is a long road, but you don’t have to travel it alone. We have a thriving community of security researchers and Immunefi team members ready to help you get there.
I invite you to become one of them, and if you’d like to work with them, you can get in touch with Immunefi here.
If you like my blog, please subscribe & share it with your friends. I write in my free time, so seeing more people read these posts motivates me to write more. I don’t send anything except my writing.